| REMOTE DESKTOP | |
| SUPPORT SERVICE | |
| New PC OS Setup | |
| New Antivirus setup | |
| MS Office installation | |
| Peripheral Setup | |
| Antivirus Removal | |
| PC Optimization | |
| Router Configuration | |
| Data transfer | |
| PC Trobleshooting | |
| Tablet setup | |

Firewall Security
1. What is a Firewall and how it protects your IT?
2. How a firewall functions?
3. The history and different generations of firewall technology?
4. What are the benefits of a firewall technology?
5. How CompuMate can help you with Firewall technology implementation?.
2. How a firewall functions?
3. The history and different generations of firewall technology?
4. What are the benefits of a firewall technology?
5. How CompuMate can help you with Firewall technology implementation?.
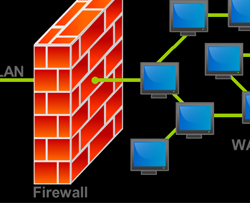 What is a Firewall?
What is a Firewall?A firewall is a part of a computer system or network that is designed to block unauthorized access while permitting authorized communications. It is a device or set of devices which is configured to permit or deny computer applications based upon a set of rules and other criteria.Firewalls can be implemented in either hardware or software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.
There are several types of firewall techniques:
Packet filter: Packet filtering inspects each packet passing through the network and accepts or rejects it based on user-defined rules. Although difficult to configure, it is fairly effective and mostly transparent to its users. It is susceptible to IP spoofing. Application gateway: Applies security mechanisms to specific applications, such as FTP and Telnet servers. This is very effective, but can impose performance degradation. Circuit-level gateway: Applies security mechanisms when a TCP or UDP connection is established. Once the connection has been made, packets can flow between the hosts without further checking. Proxy server: Intercepts all messages entering and leaving the network. The proxy server effectively hides the true network addresses.
How a Firewall Functions?
A firewall is a dedicated appliance, or software running on a computer, which inspects network traffic passing through it, and denies or permits passage based on a set of rules/criteria. It is normally placed between a protected network and an unprotected network and acts like a gate to protect assets to ensure that nothing private goes out and nothing malicious comes in. A firewall's basic task is to regulate some of the flow of traffic between computer networks of different trust levels. Typical examples are the Internet which is a zone with no trust and internal network which is a zone of higher trust. A zone with an intermediate trust level, situated between the Internet and a trusted internal network, is often referred to as a "perimeter network" or Demilitarized zone (DMZ). A firewall's function within a network is similar to physical firewalls with fire doors in building construction. In the former case, it is used to prevent network intrusion to the private network. In the latter case, it is intended to contain and delay structural fire from spreading to adjacent structures.
History
The term firewall/fireblock originally meant a wall to confine a fire or potential fire within a building; cf. firewall (construction) . Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The Morris Worm spread itself through multiple vulnerabilities in the machines of the time. Although it was not malicious in intent, the Morris Worm was the first large scale attack on Internet security; the online community was neither expecting an attack nor prepared to deal with one.
First generation: packet filters
The first paper published on firewall technology was in 1988, when engineers from Digital Equipment Corporation (DEC) developed filter systems known as packet filter firewalls. This fairly basic system was the first generation of what became a highly evolved and technical internet security feature. At AT&T Bell Labs, Bill Cheswick and Steve Bellovin were continuing their research in packet filtering and developed a working model for their own company based upon their original first generation architecture. This type of packet filtering pays no attention to whether a packet is part of an existing stream of traffic (it stores no information on connection "state"). Instead, it filters each packet based only on information contained in the packet itself (most commonly using a combination of the packet's source and destination address, its protocol, and, for TCP and UDP traffic, the port number).
TCP and UDP protocols comprise most communication over the Internet, and because TCP and UDP traffic by convention uses well known ports for particular types of traffic, a "stateless" packet filter can distinguish between, and thus control, those types of traffic (such as web browsing, remote printing, email transmission, file transfer), unless the machines on each side of the packet filter are both using the same non-standard ports. Packet filtering firewalls work on the first three layers of the OSI reference model, which means all the work is done between the network and physical layers. When a packet originates from the sender and filters through a firewall, the device checks for matches to any of the packet filtering rules that are configured in the firewall and drops or rejects the packet accordingly. When the packet passes through the firewall it filters the packet on a protocol/port number basis (GSS). For example if a rule in the firewall exists to block telnet access, then the firewall will block the IP protocol for port number 23.
Second generation:
application layer The key benefit of application layer filtering is that it can "understand" certain applications and protocols (such as File Transfer Protocol, DNS, or web browsing), and it can detect if an unwanted protocol is sneaking through on a non-standard port or if a protocol is being abused in any harmful way. An application firewall is much more secure and reliable compared to packet filter firewalls because it works on all seven layers of the OSI reference model, from the application down to the physical Layer. This is similar to a packet filter firewall but here we can also filter information on the basis of content. The best example of an application firewall is ISA (Internet Security and Acceleration) server. An application firewall can filter higher-layer protocols such as FTP, Telnet, DNS, DHCP, HTTP, TCP, UDP and TFTP (GSS). For example, if an organization wants to block all the information related to "foo" then content filtering can be enabled on the firewall to block that particular word. Software-based firewalls are thus much slower than stateful firewalls.
Third generation: "stateful" filters
From 1989-1990 three colleagues from AT&T Bell Laboratories, Dave Presetto, Janardan Sharma, and Kshitij Nigam, developed the third generation of firewalls, calling them circuit level firewalls. Third-generation firewalls, in addition to what first- and secondgeneration look for, regard placement of each individual packet within the packet series. This technology is generally referred to as a stateful packet inspection as it maintains records of all connections passing through the firewall and is able to determine whether a packet is the start of a new connection, a part of an existing connection, or is an invalid packet. Though there is still a set of static rules in such a firewall, the state of a connection can itself be one of the criteria which trigger specific rules. This type of firewall can actually be exploiting by certain Denial-of-service attacks which can fill the connection tables with illegitimate connections.
Types
There are several classifications of firewalls depending on where the communication is taking place, where the communication is intercepted and the state that is being traced.
Network layer and packet filters
Network layer firewalls, also called packet filters, operate at a relatively low level of the TCP/IP protocol stack, not allowing packets to pass through the firewall unless they match the established rule set. The firewall administrator may define the rules; or default rules may apply. The term "packet filter" originated in the context of BSD operating systems. Network layer firewalls generally fall into two sub-categories, stateful and stateless. Stateful firewalls maintain context about active sessions, and use that "state information" to speed packet processing. Any existing network connection can be described by several properties, including source and destination IP address, UDP or TCP ports, and the current stage of the connection's lifetime (including session initiation, handshaking, data transfer, or completion connection). If a packet does not match an existing connection, it will be evaluated according to the rule set for new connections. If a packet matches an existing connection based on comparison with the firewall's state table, it will be allowed to pass without further processing. Stateless firewalls require less memory, and can be faster for simple filters that require less time to filter than to look up a session. They may also be necessary for filtering stateless network protocols that have no concept of a session.
However, they cannot make more complex decisions based on what stage communications between hosts have reached. Modern firewalls can filter traffic based on many packet attributes like source IP address, source port, destination IP address or port, destination service like WWW or FTP. They can filter based on protocols, TTL values, net block of originator, of the source, and many other attributes. Application-layer firewalls work on the application level of the TCP/IP stack (i.e., all browser traffic, or all telnet or ftp traffic), and may intercept all packets traveling to or from an application. They block other packets (usually dropping them without acknowledgment to the sender). In principle, application firewalls can prevent all unwanted outside traffic from reaching protected machines. On inspecting all packets for improper content, firewalls can restrict or prevent outright the spread of networked computer worms and Trojans. The additional inspection criteria can add extra latency to the forwarding of packets to their destination.
Proxies
A proxy device (running either on dedicated hardware or as software on a general-purpose machine) may act as a firewall by responding to input packets (connection requests, for example) in the manner of an application, whilst blocking other packets. Proxies make tampering with an internal system from the external network more difficult and misuse of one internal system would not necessarily cause a security breach exploitable from outside the firewall (as long as the application proxy remains intact and properly configured). Conversely, intruders may hijack a publicly-reachable system and use it as a proxy for their own purposes; the proxy then masquerades as that system to other internal machines. While use of internal address spaces enhances security, crackers may still employ methods such as IP spoofing to attempt to pass packets to a target network.
Network address translation
Firewalls often have network address translation (NAT) functionality, and the hosts protected behind a firewall commonly have addresses in the "private address range", as defined in RFC 1918. Firewalls often have such functionality to hide the true address of protected hosts. Originally, the NAT function was developed to address the limited number of IPv4 routable addresses that could be used or assigned to companies or individuals as well as reduce both the amount and therefore cost of obtaining enough public addresses for every computer in an organization. Hiding the addresses of protected devices has become an increasingly important defense against network reconnaissance.
Benefits of a firewall technology
Firewalls protect private local area networks from hostile intrusion from the Internet. Consequently, many LANs are now connected to the Internet where Internet connectivity would otherwise have been too great a risk. Firewalls allow network administrators to offer access to specific types of Internet services to selected LAN users. This selectivity is an essential part of any information management program, and involves not only protecting private information assets, but also knowing who has access to what. Privileges can be granted according to job description and need rather than on an all-or-nothing basis. The Internet has made a large amount of information available to us. People of all age enjoy browsing websites for different purposes, whether it is for education, entertainment, for business or any other reason. Some geeks are addictive to using Internet - perhaps, their at least half of a day is spent surfing websites and for some people, having access to the information on Internet is not just an advantage but is essential.
Yet, connecting a computer or a private network to the Internet can be a security risk, the sensitive and confidential data on computer disk can be exposed to malicious attacks from a remote hacker. Therefore, it is important for computer users that they are aware of these dangers and how to protect their valuable assets and critical systems. Anyone who connects to the internet, as a single computer or whole network, should use a firewall. A Firewall can protect both - individual computers and corporate networks from dangerous attacks that may generate from internet or local network. It helps in saving valuable resources sitting on a computer disk from theft and misuse. A firewall can also log all attempts to enter private network or an individual computer. It alarms when an unauthorized, suspicious or hostile entry is attempted. Some firewalls can also monitor and log all outbound data traffic and prevent unauthorized access to resources on external networks. Firewalls have ability to filter traffic, based on their source and destination addresses, as well as port numbers. Firewalls can also filter traffic by packet state and attribute. A firewall can be configured to allow traffic through, if it is coming from a specified trusted host. Similarly, with a firewall, data traffic could be restricted from specified ports and ports can also be opened for data to enter.
Network administrators are very much benefited from using firewalls. It helps them keep away unauthorized users such as Hackers, Crackers and even banning their access to the network services and resources. Some firewalls offer protection against viruses, Trojans and viruses, too. These firewalls can detect traffic that includes malware and prevent them from entering into a computer. Firewalls provide means for administrators to monitor inbound and outbound traffic. This is very helpful to them in auditing and taking reports of all the traffic passing through the firewall. Firewalls installed on our systems give feeling of increased security that our computer and the data are safe and continuously being protected.
Firewalls are inexpensive and some are free for home users. New firewall releases are becoming easier to use and offer userfriendly interface. Windows users enjoy the free built-in firewall that comes with it. Both hardware and software firewalls are available. Both shares similar and also different much-required features. Some of the main differences in hardware and software firewalls are the following:
1- Hardware firewall protects an entire network whereas software firewall protects only a single computer. 2- Since hardware firewall does not run on the system itself, the system's performance, therefore, is not affected. 3- Software firewalls are cheap and even free for home users, whereas, hardware firewalls are comparatively more expensive. After reading the abovementioned benefits of having a firewall, it can be concluded that a firewall is a "must have" security product, without which, our computers can be exposed to intentional hostile intrusion.:
CompuMate @ Firewall
CompuMate's expertize, the knowledge are an asset to anyone who believes in quality and reliable technology solutions. We can advise, plan and implement firewall technology solutions at your business environment too - let it be small or big , simple or complex nature of networks.
| Next Step |
To discuss how Compumate Support Services
could benifit your business, please contact us
could benifit your business, please contact us
And if you'd like to know more about how we support our
clients, just call or mail us;
Call : +971 4 4344200
Mail us : sales@compumate.ae